
Ucertify H12-711_V3.0 Questions are updated and all H12-711_V3.0 answers are verified by experts. Once you have completely prepared with our H12-711_V3.0 exam prep kits you will be ready for the real H12-711_V3.0 exam without a problem. We have Up to the minute HUAWEI H12-711_V3.0 dumps study guide. PASSED H12-711_V3.0 First attempt! Here What I Did.
Online HUAWEI H12-711_V3.0 free dumps demo Below:
NEW QUESTION 1
Which of the following are the response actions of gateway anti-virus after detecting email virus? (multiple choice)
Answer: ABCD
NEW QUESTION 2
Regarding the statement of firewall security policy, which of the following options is false?
Answer: A
NEW QUESTION 3
Compared with IPSec VPN, ( ) has the advantage of good compatibility and can encapsulate IPX, multicast packets, etc., and is widely used. (fill in the blank)
Answer: A
NEW QUESTION 4
Drag the phases of the cybersecurity emergency response on the left into the box on the right, and arrange them from top to bottom in the order of execution.[fill in the blank]*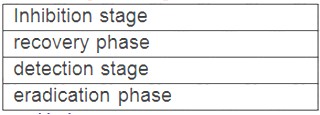
Answer: A
NEW QUESTION 5
Which of the following security threats are terminal security threats? (multiple choice)
Answer: BCD
NEW QUESTION 6
When an enterprise establishes its own information system, it checks each operation according to the authoritative standards formulated by the international, and can check whether its own information system is safe or not.
Answer: A
NEW QUESTION 7
Which of the following is not a stand-alone anti-virus technology? ( )[Multiple choice]*
Answer: B
NEW QUESTION 8
Which of the following options areSSL VPNfunction? (multiple choice)
Answer: AC
NEW QUESTION 9
NAPTtechnology can realize a public networkIPThe address is used by multiple private network hosts
Answer: A
NEW QUESTION 10
Which of the following traffic matches the authentication policy will trigger authentication?
Answer: C
NEW QUESTION 11
aboutNATAddress translation, which of the following statements is europium false??
Answer: D
NEW QUESTION 12
aboutVPN, which of the following statements is false?
Answer: B
NEW QUESTION 13
Database operation records can be used as ______ evidence to backtrack security events.[fill in the blank]*
Answer: A
NEW QUESTION 14
Which of the following descriptions about digital fingerprints in digital signatures is wrong? ( )[Multiple choice]*
Answer: C
NEW QUESTION 15
When a network security incident occurs, investigate the intrusion behavior, virus or Trojan horse, and repair and strengthen the host. Which of the above actions belong to the work content of the network security emergency response?
Answer: D
NEW QUESTION 16
A digital envelope refers to the data obtained by the sender using the receiver's ______ to encrypt the symmetric key[fill in the blank]*
Answer: A
NEW QUESTION 17
......
P.S. Easily pass H12-711_V3.0 Exam with 492 Q&As Allfreedumps.com Dumps & pdf Version, Welcome to Download the Newest Allfreedumps.com H12-711_V3.0 Dumps: https://www.allfreedumps.com/H12-711_V3.0-dumps.html (492 New Questions)