
Master the CS0-002 CompTIA Cybersecurity Analyst (CySA+) Certification Exam content and be ready for exam day success quickly with this Passleader CS0-002 real exam. We guarantee it!We make it a reality and give you real CS0-002 questions in our CompTIA CS0-002 braindumps.Latest 100% VALID CompTIA CS0-002 Exam Questions Dumps at below page. You can use our CompTIA CS0-002 braindumps and pass your exam.
Check CS0-002 free dumps before getting the full version:
NEW QUESTION 1
As part of a merger with another organization, a Chief Information Security Officer (CISO) is working with an assessor to perform a risk assessment focused on data privacy compliance. The CISO is primarily concerned with the potential legal liability and fines associated with data privacy. Based on the CISO's concerns, the assessor will MOST likely focus on:
Answer: D
NEW QUESTION 2
A security technician is testing a solution that will prevent outside entities from spoofing the company's email domain, which is comptia.org. The testing is successful, and the security technician is prepared to fully implement the solution.
Which of the following actions should the technician take to accomplish this task?
Answer: A
NEW QUESTION 3
While preparing of an audit of information security controls in the environment an analyst outlines a framework control that has the following requirements:
• All sensitive data must be classified
• All sensitive data must be purged on a quarterly basis
• Certificates of disposal must remain on file for at least three years
This framework control is MOST likely classified as:
Answer: A
NEW QUESTION 4
A security analyst has discovered trial developers have installed browsers on all development servers in the company's cloud infrastructure and are using them to browse the Internet. Which of the following changes should the security analyst make to BEST protect the environment?
Answer: A
NEW QUESTION 5
A security analyst needs to assess the web server versions on a list of hosts to determine which are running a vulnerable version of the software and output that list into an XML file named Webserverlist. Xml. The host list is provided in a file named werbserverlist,text. Which of the fallowing Nmap commands would BEST accomplish this goal?
A)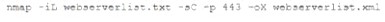
B)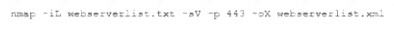
C)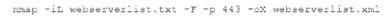
D)
Answer: A
NEW QUESTION 6
A security analyst on the threat-hunting team has developed a list of unneeded, benign services that are currently running as part of the standard OS deployment for workstations. The analyst will provide this list to the operations team to create a policy that will automatically disable the services for all workstations in the organization.
Which of the following BEST describes the security analyst's goal?
Answer: B
NEW QUESTION 7
Which of the following roles is ultimately responsible for determining the classification levels assigned to specific data sets?
Answer: B
NEW QUESTION 8
A security analyst was alerted to a tile integrity monitoring event based on a change to the vhost-paymonts .c onf file The output of the diff command against the known-good backup reads as follows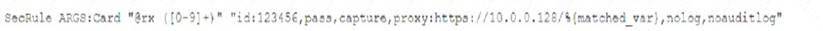
Which of the following MOST likely occurred?
Answer: A
NEW QUESTION 9
Which of the following technologies can be used to house the entropy keys for task encryption on desktops and laptops?
Answer: A
NEW QUESTION 10
An organization was alerted to a possible compromise after its proprietary data was found for sale on the Internet. An analyst is reviewing the logs from the next-generation UTM in an attempt to find evidence of this breach. Given the following output: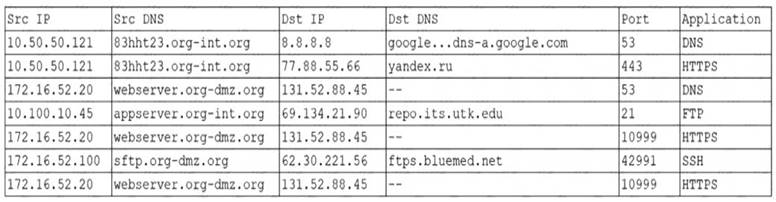
Which of the following should be the focus of the investigation?
Answer: A
NEW QUESTION 11
A development team uses open-source software and follows an Agile methodology with two-week sprints. Last month, the security team filed a bug for an insecure version of a common library. The DevOps team updated the library on the server, and then the security team rescanned the server to verify it was no longer vulnerable. This month, the security team found the same vulnerability on the server.
Which of the following should be done to correct the cause of the vulnerability?
Answer: B
NEW QUESTION 12
A security analyst at a technology solutions firm has uncovered the same vulnerabilities on a vulnerability scan for a long period of time. The vulnerabilities are on systems that are dedicated to the firm's largest client. Which of the following is MOST likely inhibiting the remediation efforts?
Answer: D
NEW QUESTION 13
A SIEM solution alerts a security analyst of a high number of login attempts against the company's webmail portal. The analyst determines the login attempts used credentials from a past data breach. Which of the following is the BEST mitigation to prevent unauthorized access?
Answer: E
NEW QUESTION 14
A security analyst receives an alert that highly sensitive information has left the company's network Upon investigation, the analyst discovers an outside IP range has had connections from three servers more than 100 times m the past month The affected servers are virtual machines Which of the following is the BEST course of action?
Answer: A
NEW QUESTION 15
A security analyst received a SIEM alert regarding high levels of memory consumption for a critical system. After several attempts to remediate the issue, the system went down. A root cause analysis revealed a bad actor forced the application to not reclaim memory. This caused the system to be depleted of resources.
Which of the following BEST describes this attack?
Answer: B
NEW QUESTION 16
......
Recommend!! Get the Full CS0-002 dumps in VCE and PDF From Certleader, Welcome to Download: https://www.certleader.com/CS0-002-dumps.html (New 186 Q&As Version)