
It is more faster and easier to pass the CompTIA CS0-002 exam by using Highest Quality CompTIA CompTIA Cybersecurity Analyst (CySA+) Certification Exam questuins and answers. Immediate access to the Down to date CS0-002 Exam and find the same core area CS0-002 questions with professionally verified answers, then PASS your exam with a high score now.
Check CS0-002 free dumps before getting the full version:
NEW QUESTION 1
Which of the following BEST describes the process by which code is developed, tested, and deployed in small batches?
Answer: A
NEW QUESTION 2
Risk management wants IT to implement a solution that will permit an analyst to intercept, execute, and analyze potentially malicious files that are downloaded from the Internet.
Which of the following would BEST provide this solution?
Answer: D
NEW QUESTION 3
A security analyst has discovered trial developers have installed browsers on all development servers in the company's cloud infrastructure and are using them to browse the Internet. Which of the following changes should the security analyst make to BEST protect the environment?
Answer: A
NEW QUESTION 4
Which of the following are components of the intelligence cycle? (Select TWO.)
Answer: BE
NEW QUESTION 5
A malicious hacker wants to gather guest credentials on a hotel 802.11 network. Which of the following tools is the malicious hacker going to use to gain access to information found on the hotel network?
Answer: A
NEW QUESTION 6
While planning segmentation for an ICS environment, a security engineer determines IT resources will need access to devices within the ICS environment without compromising security.
To provide the MOST secure access model in this scenario, the jumpbox should be.
Answer: D
NEW QUESTION 7
Which of the following software assessment methods would be BEST for gathering data related to an application’s availability during peak times?
Answer: B
NEW QUESTION 8
A cybersecurity analyst is supposing an incident response effort via threat intelligence. Which of the following is the analyst MOST likely executing?
Answer: D
NEW QUESTION 9
After receiving reports latency, a security analyst performs an Nmap scan and observes the following output: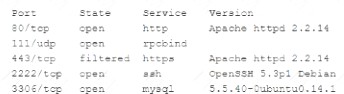
Which of the following suggests the system that produced output was compromised?
Answer: B
NEW QUESTION 10
An analyst is working with a network engineer to resolve a vulnerability that was found in a piece of legacy hardware, which is critical to the operation of the organization's production line. The legacy hardware does not have third-party support, and the OEM manufacturer of the controller is no longer in operation. The analyst documents the activities and verifies these actions prevent remote exploitation of the vulnerability.
Which of the following would be the MOST appropriate to remediate the controller?
Answer: A
NEW QUESTION 11
A company's marketing emails are either being found in a spam folder or not being delivered at all. The security analyst investigates the issue and discovers the emails in question are being sent on behalf of the company by a third party in1marketingpartners.com Below is the exiting SPP word:
Which of the following updates to the SPF record will work BEST to prevent the emails from being marked as spam or blocked?
A)
B)
C)
D)
Answer: B
NEW QUESTION 12
A security administrator needs to create an IDS rule to alert on FTP login attempts by root. Which of the following rules is the BEST solution?
Answer: B
NEW QUESTION 13
A hybrid control is one that:
Answer: B
NEW QUESTION 14
A security analyst received an email with the following key: Xj3XJ3LLc
A second security analyst received an email with following key: 3XJ3xjcLLC
The security manager has informed the two analysts that the email they received is a key that allows access to the company’s financial segment for maintenance. This is an example of:
Answer: A
NEW QUESTION 15
A pharmaceutical company's marketing team wants to send out notifications about new products to alert users of recalls and newly discovered adverse drug reactions. The team plans to use the names and mailing addresses that users have provided.
Which of the following data privacy standards does this violate?
Answer: A
NEW QUESTION 16
An organization developed a comprehensive modern response policy Executive management approved the policy and its associated procedures. Which of the following activities would be MOST beneficial to evaluate personnel's familiarity with incident response procedures?
Answer: A
NEW QUESTION 17
The inability to do remote updates of certificates, keys, software, and firmware is a security issue commonly associated with:
Answer: D
NEW QUESTION 18
Approximately 100 employees at your company have received a phishing email. As a security analyst you have been tasked with handling this situation.
INSTRUCTIONS
Review the information provided and determine the following:
* 1. How many employees clicked on the link in the phishing email?
* 2. On how many workstations was the malware installed?
* 3. What is the executable file name or the malware?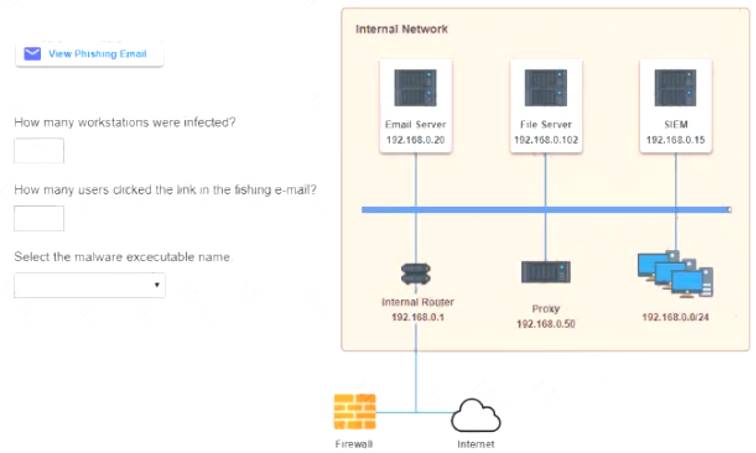
Answer: A
NEW QUESTION 19
......
P.S. Easily pass CS0-002 Exam with 220 Q&As Dumps-files.com Dumps & pdf Version, Welcome to Download the Newest Dumps-files.com CS0-002 Dumps: https://www.dumps-files.com/files/CS0-002/ (220 New Questions)