
Act now and download your EC-Council 312-50v11 test today! Do not waste time for the worthless EC-Council 312-50v11 tutorials. Download Renovate EC-Council Certified Ethical Hacker Exam (CEH v11) exam with real questions and answers and begin to learn EC-Council 312-50v11 with a classic professional.
Free 312-50v11 Demo Online For EC-Council Certifitcation:
NEW QUESTION 1
A bank stores and processes sensitive privacy information related to home loans. However, auditing has never been enabled on the system. What is the first step that the bank should take before enabling the audit feature?
Answer: B
NEW QUESTION 2
Hackers often raise the trust level of a phishing message by modeling the email to look similar to the internal email used by the target company. This includes using logos, formatting, and names of the target company. The phishing message will often use the name of the company CEO, President, or Managers. The time a hacker spends performing research to locate this information about a company is known as?
Answer: C
NEW QUESTION 3
Why containers are less secure that virtual machines?
Answer: A
NEW QUESTION 4
What is one of the advantages of using both symmetric and asymmetric cryptography in SSL/TLS?
Answer: A
NEW QUESTION 5
During an Xmas scan what indicates a port is closed?
Answer: B
NEW QUESTION 6
An attacker has installed a RAT on a host. The attacker wants to ensure that when a user attempts to go to "www.MyPersonalBank.com", the user is directed to a phishing site.
Which file does the attacker need to modify?
Answer: D
NEW QUESTION 7
Your company was hired by a small healthcare provider to perform a technical assessment on the network. What is the best approach for discovering vulnerabilities on a Windows-based computer?
Answer: B
NEW QUESTION 8
What does a firewall check to prevent particular ports and applications from getting packets into an organization?
Answer: A
NEW QUESTION 9
What is the role of test automation in security testing?
Answer: D
NEW QUESTION 10
You have successfully comprised a server having an IP address of 10.10.0.5. You would like to enumerate all machines in the same network quickly.
What is the best Nmap command you will use?
Answer: B
NEW QUESTION 11
Study the snort rule given below: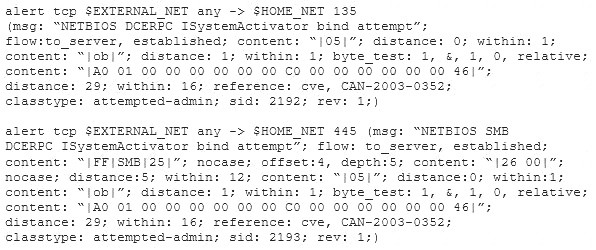
From the options below, choose the exploit against which this rule applies.
Answer: C
NEW QUESTION 12
You are trying to break into a highly classified top-secret mainframe computer with highest security system in place at Merclyn Barley Bank located in Los Angeles.
You know that conventional hacking doesn't work in this case, because organizations such as banks are generally tight and secure when it comes to protecting their systems.
In other words, you are trying to penetrate an otherwise impenetrable system. How would you proceed?
Answer: B
NEW QUESTION 13
Which of the following tools can be used for passive OS fingerprinting?
Answer: B
NEW QUESTION 14
An incident investigator asks to receive a copy of the event logs from all firewalls, proxy servers, and Intrusion Detection Systems (IDS) on the network of an organization that has experienced a possible breach of security. When the investigator attempts to correlate the information in all of the logs, the sequence of many of the logged events do not match up.
What is the most likely cause?
Answer: A
NEW QUESTION 15
Scenario1:
* 1. Victim opens the attacker's web site.
* 2. Attacker sets up a web site which contains interesting and attractive content like 'Do you want to make
$1000 in a day?'.
* 3. Victim clicks to the interesting and attractive content URL.
* 4. Attacker creates a transparent 'iframe' in front of the URL which victim attempts to click, so victim thinks that he/she clicks to the 'Do you want to make $1000 in a day?' URL but actually he/she clicks to the content or URL that exists in the transparent 'iframe' which is setup by the attacker.
What is the name of the attack which is mentioned in the scenario?
Answer: D
NEW QUESTION 16
During the process of encryption and decryption, what keys are shared? During the process of encryption and decryption, what keys are shared?
Answer: C
NEW QUESTION 17
Joseph was the Web site administrator for the Mason Insurance in New York, who's main Web site was located at www.masonins.com. Joseph uses his laptop computer regularly to administer the Web site. One night, Joseph received an urgent phone call from his friend, Smith. According to Smith, the main Mason Insurance web site had been vandalized! All of its normal content was removed and replaced with an attacker's message ''Hacker Message: You are dead! Freaks!” From his office, which was directly connected to Mason Insurance's internal network, Joseph surfed to the Web site using his laptop. In his browser, the Web site looked completely intact.
No changes were apparent. Joseph called a friend of his at his home to help troubleshoot the problem. The Web site appeared defaced when his friend visited using his DSL connection. So, while Smith and his friend could see the defaced page, Joseph saw the intact Mason Insurance web site. To help make sense of this problem, Joseph decided to access the Web site using hisdial-up ISP. He disconnected his laptop from the corporate internal network and used his modem to dial up the same ISP used by Smith. After his modem connected, he quickly typed www.masonins.com in his browser to reveal the following web page: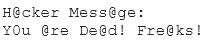
After seeing the defaced Web site, he disconnected his dial-up line, reconnected to the internal network, and used Secure Shell (SSH) to log in directly to the Web server. He ran Tripwire against the entire Web site, and determined that every system file and all the Web content on the server were intact. How did the attacker accomplish this hack?
Answer: C
NEW QUESTION 18
Which regulation defines security and privacy controls for Federal information systems and organizations?
Answer: D
NEW QUESTION 19
Which is the first step followed by Vulnerability Scanners for scanning a network?
Answer: D
NEW QUESTION 20
You receive an e-mail like the one shown below. When you click on the link contained in the mail, you are redirected to a website seeking you to download free Anti-Virus software.
Dear valued customers,
We are pleased to announce the newest version of Antivirus 2010 for Windows which will probe you with total security against the latest spyware, malware, viruses, Trojans and other online threats. Simply visit the link below and enter your antivirus code: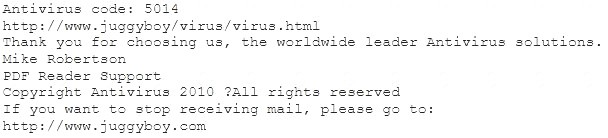
or you may contact us at the following address: Media Internet Consultants, Edif. Neptuno, Planta
Baja, Ave. Ricardo J. Alfaro, Tumba Muerto, n/a Panama
How will you determine if this is Real Anti-Virus or Fake Anti-Virus website?
Answer: C
NEW QUESTION 21
Which of the following tools is used to detect wireless LANs using the 802.11a/b/g/n WLAN standards on a linux platform?
Answer: A
NEW QUESTION 22
Which of the following represents the initial two commands that an IRC client sends to join an IRC network?
Answer: A
NEW QUESTION 23
Which of the following viruses tries to hide from anti-virus programs by actively altering and corrupting the chosen service call interruptions when they are being run?
Answer: B
NEW QUESTION 24
How is the public key distributed in an orderly, controlled fashion so that the users can be sure of the sender’s identity?
Answer: D
NEW QUESTION 25
......
100% Valid and Newest Version 312-50v11 Questions & Answers shared by Thedumpscentre.com, Get Full Dumps HERE: https://www.thedumpscentre.com/312-50v11-dumps/ (New 254 Q&As)