
Your success in EC-Council 312-50v11 is our sole target and we develop all our 312-50v11 braindumps in a way that facilitates the attainment of this target. Not only is our 312-50v11 study material the best you can find, it is also the most detailed and the most updated. 312-50v11 Practice Exams for EC-Council 312-50v11 are written to the highest standards of technical accuracy.
Free demo questions for EC-Council 312-50v11 Exam Dumps Below:
NEW QUESTION 1
What is correct about digital signatures?
Answer: A
NEW QUESTION 2
Eve is spending her day scanning the library computers. She notices that Alice is using a computer whose port 445 is active and listening. Eve uses the ENUM tool to enumerate Alice machine. From the command prompt, she types the following command.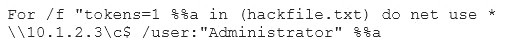
What is Eve trying to do?
Answer: C
NEW QUESTION 3
The following is an entry captured by a network IDS. You are assigned the task of analyzing this entry. You notice the value 0x90, which is the most common NOOP instruction for the Intel processor. You figure that the attacker is attempting a buffer overflow attack.
You also notice "/bin/sh" in the ASCII part of the output. As an analyst what would you conclude about the attack?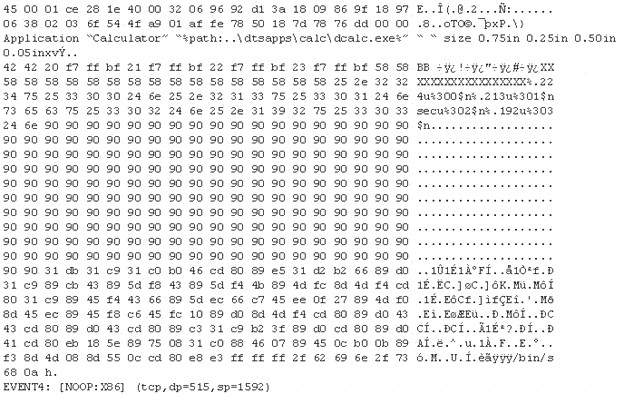
Answer: D
NEW QUESTION 4
The network administrator at Spears Technology, Inc has configured the default gateway Cisco router's access-list as below:
You are hired to conduct security testing on their network.
You successfully brute-force the SNMP community string using a SNMP crack tool.
The access-list configured at the router prevents you from establishing a successful connection. You want to retrieve the Cisco configuration from the router. How would you proceed?
Answer: BD
NEW QUESTION 5
What term describes the amount of risk that remains after the vulnerabilities are classified and the countermeasures have been deployed?
Answer: A
NEW QUESTION 6
Switches maintain a CAM Table that maps individual MAC addresses on the network to physical ports on the switch.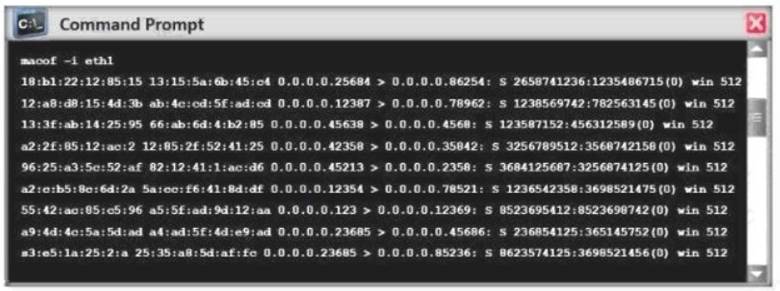
In MAC flooding attack, a switch is fed with many Ethernet frames, each containing different source MAC addresses, by the attacker. Switches have a limited memory for mapping various MAC addresses to physical ports. What happens when the CAM table becomes full?
Answer: A
NEW QUESTION 7
When a security analyst prepares for the formal security assessment - what of the following should be done in order to determine inconsistencies in the secure assets database and verify that system is compliant to the minimum security baseline?
Answer: A
NEW QUESTION 8
What port number is used by LDAP protocol?
Answer: B
NEW QUESTION 9
A technician is resolving an issue where a computer is unable to connect to the Internet using a wireless access point. The computer is able to transfer files locally to other machines, but cannot successfully reach the Internet. When the technician examines the IP address and default gateway they are both on the 192.168.1.0/24. Which of the following has occurred?
Answer: B
NEW QUESTION 10
Identify the correct terminology that defines the above statement.
Answer: B
NEW QUESTION 11
While performing online banking using a Web browser, a user receives an email that contains a link to an interesting Web site. When the user clicks on the link, another Web browser session starts and displays a video of cats playing a piano. The next business day, the user receives what looks like an email from his bank, indicating that his bank account has been accessed from a foreign country. The email asks the user to call his bank and verify the authorization of a funds transfer that took place. What Web browser-based security vulnerability was exploited to compromise the user?
Answer: C
NEW QUESTION 12
Which of the following programs is usually targeted at Microsoft Office products?
Answer: C
NEW QUESTION 13
What is GINA?
Answer: D
NEW QUESTION 14
An attacker runs netcat tool to transfer a secret file between two hosts.
He is worried about information being sniffed on the network.
How would the attacker use netcat to encrypt the information before transmitting onto the wire?
Answer: D
NEW QUESTION 15
OpenSSL on Linux servers includes a command line tool for testing TLS. What is the name of the tool and the correct syntax to connect to a web server?
Answer: C
NEW QUESTION 16
Which address translation scheme would allow a single public IP address to always correspond to a single machine on an internal network, allowing "server publishing"?
Answer: D
NEW QUESTION 17
Which Intrusion Detection System is the best applicable for large environments where critical assets on the network need extra scrutiny and is ideal for observing sensitive network segments?
Answer: C
NEW QUESTION 18
In the field of cryptanalysis, what is meant by a “rubber-hose” attack?
Answer: C
NEW QUESTION 19
Which results will be returned with the following Google search query? site:target.com – site:Marketing.target.com accounting
Answer: D
NEW QUESTION 20
Null sessions are un-authenticated connections (not using a username or password.) to an NT or 2000 system. Which TCP and UDP ports must you filter to check null sessions on your network?
Answer: D
NEW QUESTION 21
Jim’s company regularly performs backups of their critical servers. But the company cannot afford to send backup tapes to an off-site vendor for long-term storage and archiving. Instead, Jim’s company keeps the backup tapes in a safe in the office. Jim’s company is audited each year, and the results from this year’s audit show a risk because backup tapes are not stored off-site. The Manager of Information Technology has a plan to take the backup tapes home with him and wants to know what two things he can do to secure the backup tapes while in transit?
Answer: A
NEW QUESTION 22
Which of the following is an extremely common IDS evasion technique in the web world?
Answer: C
NEW QUESTION 23
You are tasked to configure the DHCP server to lease the last 100 usable IP addresses in subnet to. 1.4.0/23. Which of the following IP addresses could be teased as a result of the new configuration?
Answer: C
NEW QUESTION 24
Let's imagine three companies (A, B and C), all competing in a challenging global environment. Company A and B are working together in developing a product that will generate a major competitive advantage for them. Company A has a secure DNS server while company B has a DNS server vulnerable to spoofing. With a spoofing attack on the DNS server of company B, company C gains access to outgoing e-mails from company B. How do you prevent DNS spoofing?
Answer: C
NEW QUESTION 25
......
Recommend!! Get the Full 312-50v11 dumps in VCE and PDF From Dumps-hub.com, Welcome to Download: https://www.dumps-hub.com/312-50v11-dumps.html (New 254 Q&As Version)