
Passleader 312-50v11 Questions are updated and all 312-50v11 answers are verified by experts. Once you have completely prepared with our 312-50v11 exam prep kits you will be ready for the real 312-50v11 exam without a problem. We have Improve EC-Council 312-50v11 dumps study guide. PASSED 312-50v11 First attempt! Here What I Did.
Free demo questions for EC-Council 312-50v11 Exam Dumps Below:
NEW QUESTION 1
As a securing consultant, what are some of the things you would recommend to a company to ensure DNS security?
Answer: BCDE
NEW QUESTION 2
A network admin contacts you. He is concerned that ARP spoofing or poisoning might occur on his network. What are some things he can do to prevent it? Select the best answers.
Answer: ABD
NEW QUESTION 3
Some clients of TPNQM SA were redirected to a malicious site when they tried to access the TPNQM main site. Bob, a system administrator at TPNQM SA, found that they were victims of DNS Cache Poisoning. What should Bob recommend to deal with such a threat?
Answer: B
NEW QUESTION 4
Gavin owns a white-hat firm and is performing a website security audit for one of his clients. He begins by running a scan which looks for common misconfigurations and outdated software versions. Which of the following tools is he most likely using?
Answer: B
NEW QUESTION 5
Peter, a Network Administrator, has come to you looking for advice on a tool that would help him perform SNMP enquires over the network.
Which of these tools would do the SNMP enumeration he is looking for? Select the best answers.
Answer: ABD
NEW QUESTION 6
Which of the following is the structure designed to verify and authenticate the identity of individuals within the enterprise taking part in a data exchange?
Answer: D
NEW QUESTION 7
Within the context of Computer Security, which of the following statements describes Social Engineering best?
Answer: C
NEW QUESTION 8
You are attempting to run an Nmap port scan on a web server. Which of the following commands would result in a scan of common ports with the least amount of noise in order to evade IDS?
Answer: C
NEW QUESTION 9
Shellshock allowed an unauthorized user to gain access to a server. It affected many Internet-facing services, which OS did it not directly affect?
Answer: D
NEW QUESTION 10
Which system consists of a publicly available set of databases that contain domain name registration contact information?
Answer: A
NEW QUESTION 11
A regional bank hires your company to perform a security assessment on their network after a recent data breach. The attacker was able to steal financial data from the bank by compromising only a single server. Based on this information, what should be one of your key recommendations to the bank?
Answer: A
NEW QUESTION 12
Tremp is an IT Security Manager, and he is planning to deploy an IDS in his small company. He is looking for an IDS with the following characteristics: - Verifies success or failure of an attack - Monitors system activities Detects attacks that a network-based IDS fails to detect - Near real-time detection and response - Does not require additional hardware - Lower entry cost Which type of IDS is best suited for Tremp's requirements?
Answer: C
NEW QUESTION 13
E- mail scams and mail fraud are regulated by which of the following?
Answer: A
NEW QUESTION 14
Which DNS resource record can indicate how long any "DNS poisoning" could last?
Answer: B
NEW QUESTION 15
What does the –oX flag do in an Nmap scan?
Answer: C
NEW QUESTION 16
Which of the following is the best countermeasure to encrypting ransomwares?
Answer: C
NEW QUESTION 17
Which of the following is a component of a risk assessment?
Answer: A
NEW QUESTION 18
Which of the following programming languages is most susceptible to buffer overflow attacks, due to its lack of a built-in bounds checking mechanism?
Code:
#include <string.h> int main(){char buffer[8];
strcpy(buffer, ““11111111111111111111111111111””);} Output: Segmentation fault
Answer: D
NEW QUESTION 19
Which of the following is not a Bluetooth attack?
Answer: A
NEW QUESTION 20
Which service in a PKI will vouch for the identity of an individual or company?
Answer: D
NEW QUESTION 21
MX record priority increases as the number increases. (True/False.)
Answer: B
NEW QUESTION 22
When analyzing the IDS logs, the system administrator noticed an alert was logged when the external router was accessed from the administrator’s Computer to update the router configuration. What type of an alert is this?
Answer: D
NEW QUESTION 23
You have successfully logged on a Linux system. You want to now cover your trade Your login attempt may be logged on several files located in /var/log. Which file does NOT belongs to the list:
Answer: C
NEW QUESTION 24
You are programming a buffer overflow exploit and you want to create a NOP sled of 200 bytes in the program exploit.c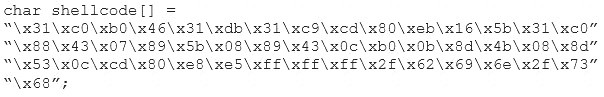
What is the hexadecimal value of NOP instruction?
Answer: D
NEW QUESTION 25
......
Thanks for reading the newest 312-50v11 exam dumps! We recommend you to try the PREMIUM Certshared 312-50v11 dumps in VCE and PDF here: https://www.certshared.com/exam/312-50v11/ (254 Q&As Dumps)