
Cause all that matters here is passing the CompTIA SY0-601 exam. Cause all that you need is a high score of SY0-601 CompTIA Security+ Exam exam. The only one thing you need to do is downloading Testking SY0-601 exam study guides now. We will not let you down with our money-back guarantee.
Check SY0-601 free dumps before getting the full version:
NEW QUESTION 1
A company has drafted an insider-threat policy that prohibits the use of external storage devices. Which of the following would BEST protect the company from data exfiltration via removable media?
Answer: D
NEW QUESTION 2
Company engineers regularly participate in a public Internet forum with other engineers throughout the industry. Which of the following tactics would an attacker MOST likely use in this scenario?
Answer: A
NEW QUESTION 3
Which of the following organizational policies are MOST likely to detect fraud that is being conducted by existing employees? (Select TWO).
Answer: BC
NEW QUESTION 4
A recent audit uncovered a key finding regarding the use of a specific encryption standard in a web application that is used to communicate with business customers. Due to the technical limitations of its customers the company is unable to upgrade the encryption standard. Which of the following types of controls should be used to reduce the risk created by this scenario?
Answer: D
NEW QUESTION 5
A company recently transitioned to a strictly BYOD culture due to the cost of replacing lost or damaged corporate-owned mobile devices. Which of the following technologies would be BEST to balance the BYOD culture while also protecting the company’s data?
Answer: C
NEW QUESTION 6
Which of the following would be the BEST resource lor a software developer who is looking to improve secure coding practices for web applications?
Answer: A
NEW QUESTION 7
In which of the following common use cases would steganography be employed?
Answer: A
NEW QUESTION 8
A user enters a password to log in to a workstation and is then prompted to enter an authentication code. Which of the following MFA factors or attributes are being utilized in the authentication process? (Select TWO).
Answer: BE
NEW QUESTION 9
An organization wants to implement a third factor to an existing multifactor authentication. The organization already uses a smart card and password. Which of the following would meet the organization’s needs for a third factor?
Answer: B
NEW QUESTION 10
A security analyst is preparing a threat for an upcoming internal penetration test. The analyst needs to identify a method for determining the tactics, techniques, and procedures of a threat against the organization’s network. Which of the following will the analyst MOST likely use to accomplish the objective?
Answer: A
NEW QUESTION 11
To secure an application after a large data breach, an e-commerce site will be resetting all users’ credentials. Which of the following will BEST ensure the site’s users are not compromised after the reset?
Answer: C
NEW QUESTION 12
A security analyst has been asked to investigate a situation after the SOC started to receive alerts from the SIEM. The analyst first looks at the domain controller and finds the following events: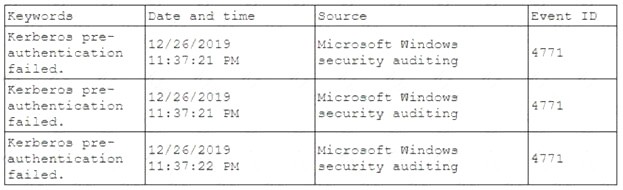
To better understand what is going on, the analyst runs a command and receives the following output: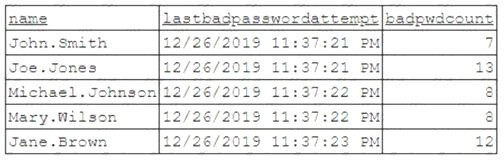
Based on the analyst’s findings, which of the following attacks is being executed?
Answer: D
NEW QUESTION 13
A security analyst is reviewing the following attack log output: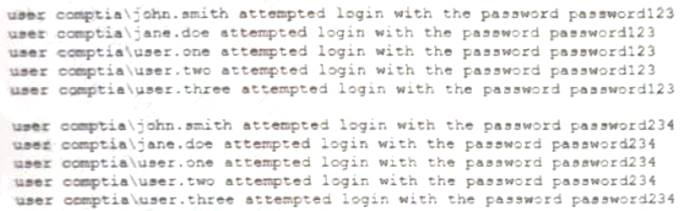
Which of the following types of attacks does this MOST likely represent?
Answer: C
NEW QUESTION 14
A company is launching a new internet platform for its clients. The company does not want to implement its own authorization solution but instead wants to rely on the authorization provided by another platform. Which of the following is the BEST approach to implement the desired solution?
Answer: D
NEW QUESTION 15
An end user reports a computer has been acting slower than normal for a few weeks. During an investigation, an analyst determines the system is sending the user's email address and a ten-digit number to an IP address once a day. The only recent log entry regarding the user's computer is the following: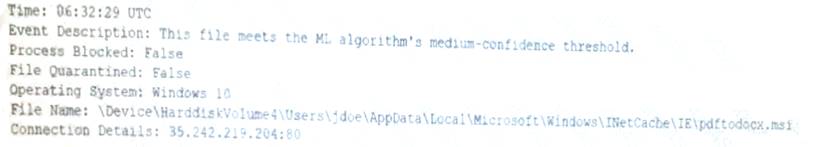
Which of the following is the MOST likely cause of the issue?
Answer: A
NEW QUESTION 16
A software developer needs to perform code-execution testing, black-box testing, and non-functional testing on a new product before its general release. Which of the following BEST describes the tasks the developer is conducting?
Answer: A
NEW QUESTION 17
Which of the following types of controls is a turnstile?
Answer: A
NEW QUESTION 18
To reduce costs and overhead, an organization wants to move from an on-premises email solution to a cloud-based email solution. At this time, no other services will be moving. Which of the following cloud models would BEST meet the needs of the organization?
Answer: D
NEW QUESTION 19
A global pandemic is forcing a private organization to close some business units and reduce staffing at others. Which of the following would be BEST to help the organization’s executives determine the next course of action?
Answer: D
NEW QUESTION 20
A security analyst reviews the datacenter access logs for a fingerprint scanner and notices an abundance of errors that correlate with users' reports of issues accessing the facility. Which of the following MOST likely the cause of the cause of the access issues?
Answer: B
NEW QUESTION 21
A smart switch has the ability to monitor electrical levels and shut off power to a building in the event of power surge or other fault situation. The switch was installed on a wired network in a hospital and is monitored by the facilities department via a cloud application. The security administrator isolated the switch on a separate VLAN and set up a patch routine. Which of the following steps should also be taken to harden the smart switch?
Answer: B
NEW QUESTION 22
Which of the following would be BEST to establish between organizations that have agreed cooperate and are engaged in early discussion to define the responsibilities of each party, but do not want to establish a contractually binding agreement?
Answer: D
NEW QUESTION 23
A security engineer needs to Implement the following requirements:
• All Layer 2 switches should leverage Active Directory tor authentication.
• All Layer 2 switches should use local fallback authentication If Active Directory Is offline.
• All Layer 2 switches are not the same and are manufactured by several vendors.
Which of the following actions should the engineer take to meet these requirements? (Select TWO).
Answer: AB
NEW QUESTION 24
......
Recommend!! Get the Full SY0-601 dumps in VCE and PDF From Certleader, Welcome to Download: https://www.certleader.com/SY0-601-dumps.html (New 218 Q&As Version)