
It is more faster and easier to pass the CompTIA SY0-601 exam by using Certified CompTIA CompTIA Security+ Exam questuins and answers. Immediate access to the Down to date SY0-601 Exam and find the same core area SY0-601 questions with professionally verified answers, then PASS your exam with a high score now.
Also have SY0-601 free dumps questions for you:
NEW QUESTION 1
An organization's RPO for a critical system is two hours. The system is used Monday through Friday, from 9:00 am to 5:00 pm. Currently, the organization performs a full backup every Saturday that takes four hours to complete. Which of the following additional backup implementations would be the BEST way for the analyst to meet the business requirements?
Answer: A
NEW QUESTION 2
A researcher has been analyzing large data sets for the last ten months. The researcher works with colleagues from other institutions and typically connects via SSH to retrieve additional data. Historically, this setup has worked without issue, but the researcher recently started getting the following message: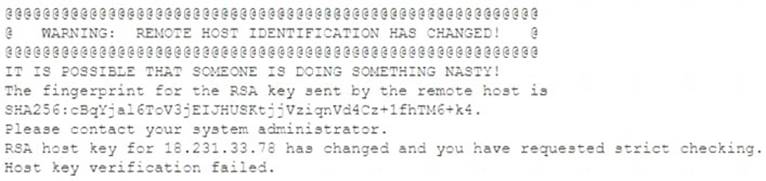
Which of the following network attacks is the researcher MOST likely experiencing?
Answer: C
NEW QUESTION 3
The IT department at a university is concerned about professors placing servers on the university network in an attempt to bypass security controls. Which of the following BEST represents this type of threat?
Answer: B
NEW QUESTION 4
A security analyst receives the configuration of a current VPN profile and notices the authentication is only applied to the IP datagram portion of the packet. Which of the following should the analyst implement to authenticate the entire packet?
Answer: B
NEW QUESTION 5
A financial organization has adopted a new secure, encrypted document-sharing application to help with its customer loan process. Some important PII needs to be shared across this new platform, but it is getting blocked by the DLP systems. Which of the following actions will BEST allow the PII to be shared with the secure application without compromising the organization’s security posture?
Answer: D
NEW QUESTION 6
During an incident response, a security analyst observes the following log entry on the web server.
Which of the following BEST describes the type of attack the analyst is experience?
Answer: B
NEW QUESTION 7
A Chief Executive Officer's (CEO) personal information was stolen in a social engineering attack. Which of the following sources would reveal if the CEO's personal information is for sale?
Answer: C
NEW QUESTION 8
A small business just recovered from a ransomware attack against its file servers by purchasing the decryption keys from the attackers. The issue was triggered by a phishing email and the IT administrator wants to ensure it does not happen again. Which of the following should the IT administrator do FIRST after recovery?
Answer: A
NEW QUESTION 9
A user recent an SMS on a mobile phone that asked for bank delays. Which of the following social-engineering techniques was used in this case?
Answer: D
NEW QUESTION 10
A security analyst is using a recently released security advisory to review historical logs, looking for the specific activity that was outlined in the advisory. Which of the following is the analyst doing?
Answer: C
NEW QUESTION 11
Some laptops recently went missing from a locked storage area that is protected by keyless RFID-enabled locks. There is no obvious damage to the physical space. The security manager identifies who unlocked the door, however, human resources confirms the employee was on vacation at the time of the incident. Which of the following describes what MOST likely occurred?
Answer: A
NEW QUESTION 12
A cybersecurity analyst reviews the log files from a web server and sees a series of files that indicates a directory-traversal attack has occurred. Which of the following is the analyst MOST likely seeing?
Answer: B
NEW QUESTION 13
A nuclear plant was the victim of a recent attack, and all the networks were air gapped. A subsequent investigation revealed a worm as the source of the issue. Which of the following BEST explains what happened?
Answer: A
NEW QUESTION 14
A security analyst needs to produce a document that details how a security incident occurred, the steps that were taken for recovery, and how future incidents can be avoided. During which of the following stages of the response process will this activity take place?
Answer: C
NEW QUESTION 15
An organization has decided to host its web application and database in the cloud Which of the following BEST describes the security concerns for this decision?
Answer: B
NEW QUESTION 16
A cybersecurity manager has scheduled biannual meetings with the IT team and department leaders to discuss how they would respond to hypothetical cyberattacks. During these meetings, the manager presents a scenario and injects additional information throughout the session to replicate what might occur in a dynamic cybersecurity event involving the company, its facilities, its data, and its staff. Which of the following describes what the manager is doing?
Answer: C
NEW QUESTION 17
A cybersecurity administrator needs to add disk redundancy for a critical server. The solution must have a two- drive failure for better fault tolerance. Which of the following RAID levels should the administrator select?
Answer: B
NEW QUESTION 18
The manager who is responsible for a data set has asked a security engineer to apply encryption to the data on a hard disk. The security engineer is an example of a:
Answer: D
NEW QUESTION 19
A user reports constant lag and performance issues with the wireless network when working at a local coffee shop. A security analyst walks the user through an installation of Wireshark and get a five-minute pcap to analyze. The analyst observes the following output: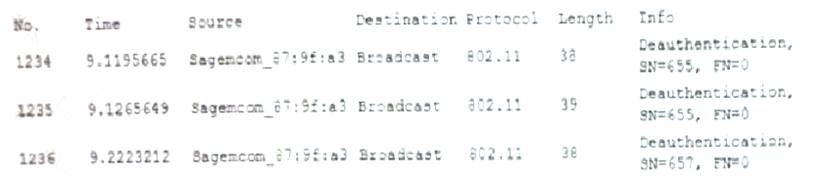
Which of the following attacks does the analyst MOST likely see in this packet capture?
Answer: B
NEW QUESTION 20
An organization routes all of its traffic through a VPN Most users are remote and connect into a corporate datacenter that houses confidential information There is a firewall at the Internet border followed by a DIP appliance, the VPN server and the datacenter itself. Which of the following is the WEAKEST design element?
Answer: C
NEW QUESTION 21
A forensics examiner is attempting to dump password cached in the physical memory of a live system but keeps receiving an error message. Which of the following BEST describes the cause of the error?
Answer: A
NEW QUESTION 22
Which of the following scenarios BEST describes a risk reduction technique?
Answer: B
NEW QUESTION 23
A security administrator currently spends a large amount of time on common security tasks, such aa report generation, phishing investigations, and user provisioning and deprovisioning This prevents the administrator from spending time on other security projects. The business does not have the budget to add more staff members. Which of the following should the administrator implement?
Answer: D
NEW QUESTION 24
......
Thanks for reading the newest SY0-601 exam dumps! We recommend you to try the PREMIUM Dumps-files.com SY0-601 dumps in VCE and PDF here: https://www.dumps-files.com/files/SY0-601/ (218 Q&As Dumps)