
Refined of SY0-601 exam engine materials and exam topics for CompTIA certification for IT specialist, Real Success Guaranteed with Updated SY0-601 pdf dumps vce Materials. 100% PASS CompTIA Security+ Exam exam Today!
Free demo questions for CompTIA SY0-601 Exam Dumps Below:
NEW QUESTION 1
A hospital's administration is concerned about a potential loss of patient data that is stored on tablets. A security administrator needs to implement controls to alert the SOC any time the devices are near exits. Which of the following would BEST achieve this objective?
Answer: D
NEW QUESTION 2
A company's Chief Information Office (CIO) is meeting with the Chief Information Security Officer (CISO) to plan some activities to enhance the skill levels of the company's developers. Which of the following would be MOST suitable for training the developers'?
Answer: B
NEW QUESTION 3
A client sent several inquiries to a project manager about the delinquent delivery status of some critical reports. The project manager darned the reports were previously sent via email but then quickly generated and backdated the reports before submitting them via a new email message Which of the following actions MOST likely supports an investigation for fraudulent submission?
Answer: D
NEW QUESTION 4
A security analyst wants to verify that a client-server (non-web) application is sending encrypted traffic. Which of the following should the analyst use?
Answer: A
NEW QUESTION 5
A company is designing the layout of a new datacenter so it will have an optimal environmental temperature Which of the following must be included? (Select TWO)
Answer: EF
NEW QUESTION 6
A company’s bank has reported that multiple corporate credit cards have been stolen over the past several weeks. The bank has provided the names of the affected cardholders to the company’s forensics team to assist in the cyber-incident investigation.
An incident responder learns the following information: The timeline of stolen card numbers corresponds closely with affected users making Internet-based purchases from diverse websites via enterprise desktop PCs.
The timeline of stolen card numbers corresponds closely with affected users making Internet-based purchases from diverse websites via enterprise desktop PCs. All purchase connections were encrypted, and the company uses an SSL inspection proxy for the inspection of encrypted traffic of the hardwired network.
All purchase connections were encrypted, and the company uses an SSL inspection proxy for the inspection of encrypted traffic of the hardwired network. Purchases made with corporate cards over the corporate guest WiFi network, where no SSL inspection occurs, were unaffected.
Purchases made with corporate cards over the corporate guest WiFi network, where no SSL inspection occurs, were unaffected.
Which of the following is the MOST likely root cause?
Answer: C
NEW QUESTION 7
Which of the following policies would help an organization identify and mitigate potential single points of failure in the company’s IT/security operations?
Answer: C
NEW QUESTION 8
A security analyst has received an alert about being sent via email. The analyst’s Chief information Security Officer (CISO) has made it clear that PII must be handle with extreme care From which of the following did the alert MOST likely originate?
Answer: B
NEW QUESTION 9
A security analyst needs to generate a server certificate to be used for 802.1X and secure RDP connections. The analyst is unsure what is required to perform the task and solicits help from a senior colleague. Which of the following is the FIRST step the senior colleague will most likely tell the analyst to perform to accomplish this task?
Answer: B
NEW QUESTION 10
An organization has a growing workforce that is mostly driven by additions to the sales department. Each newly hired salesperson relies on a mobile device to conduct business. The Chief Information Officer (CIO) is wondering it the organization may need to scale down just as quickly as it scaled up. The ClO is also concerned about the organization's security and customer privacy. Which of the following would be BEST to address the ClO’s concerns?
Answer: C
NEW QUESTION 11
During a security assessment, a security finds a file with overly permissive permissions. Which of the following tools will allow the analyst to reduce the permission for the existing users and groups and remove the set-user-ID from the file?
Answer: D
NEW QUESTION 12
The IT department at a university is concerned about professors placing servers on the university network in an attempt to bypass security controls. Which of the following BEST represents this type of threat?
Answer: B
NEW QUESTION 13
A security engineer at an offline government facility is concerned about the validity of an SSL certificate. The engineer wants to perform the fastest check with the least delay to determine if the certificate has been revoked. Which of the following would BEST these requirement?
Answer: C
NEW QUESTION 14
A global pandemic is forcing a private organization to close some business units and reduce staffing at others. Which of the following would be BEST to help the organization’s executives determine the next course of action?
Answer: D
NEW QUESTION 15
A security administrator checks the table of a network switch, which shows the following output: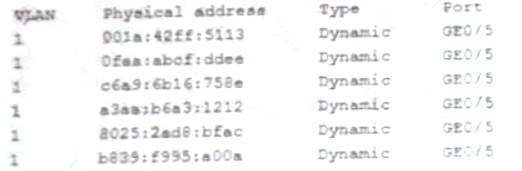
Which of the following is happening to this switch?
Answer: A
NEW QUESTION 16
A security analyst is investigating an incident to determine what an attacker was able to do on a compromised laptop. The analyst reviews the following SIEM log:
Which of the following describes the method that was used to compromise the laptop?
Answer: A
NEW QUESTION 17
Which of the following BEST explains the difference between a data owner and a data custodian?
Answer: B
NEW QUESTION 18
......
100% Valid and Newest Version SY0-601 Questions & Answers shared by Certshared, Get Full Dumps HERE: https://www.certshared.com/exam/SY0-601/ (New 402 Q&As)