
Master the SY0-601 CompTIA Security+ Exam content and be ready for exam day success quickly with this Passleader SY0-601 torrent. We guarantee it!We make it a reality and give you real SY0-601 questions in our CompTIA SY0-601 braindumps.Latest 100% VALID CompTIA SY0-601 Exam Questions Dumps at below page. You can use our CompTIA SY0-601 braindumps and pass your exam.
CompTIA SY0-601 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
A company’s bank has reported that multiple corporate credit cards have been stolen over the past several weeks. The bank has provided the names of the affected cardholders to the company’s forensics team to assist in the cyber-incident investigation.
An incident responder learns the following information: The timeline of stolen card numbers corresponds closely with affected users making Internet-based purchases from diverse websites via enterprise desktop PCs.
The timeline of stolen card numbers corresponds closely with affected users making Internet-based purchases from diverse websites via enterprise desktop PCs. All purchase connections were encrypted, and the company uses an SSL inspection proxy for the inspection of encrypted traffic of the hardwired network.
All purchase connections were encrypted, and the company uses an SSL inspection proxy for the inspection of encrypted traffic of the hardwired network. Purchases made with corporate cards over the corporate guest WiFi network, where no SSL inspection occurs, were unaffected.
Purchases made with corporate cards over the corporate guest WiFi network, where no SSL inspection occurs, were unaffected.
Which of the following is the MOST likely root cause?
Answer: C
NEW QUESTION 2
A cybersecurity department purchased o new PAM solution. The team is planning to randomize the service account credentials of the Windows server first. Which of the following would be the BEST method to increase the security on the Linux server?
Answer: C
NEW QUESTION 3
A security engineer is reviewing log files after a third discovered usernames and passwords for the organization’s accounts. The engineer sees there was a change in the IP address for a vendor website one earlier. This change lasted eight hours. Which of the following attacks was MOST likely used?
Answer: D
NEW QUESTION 4
A security assessment determines DES and 3DES at still being used on recently deployed production servers. Which of the following did the assessment identify?
Answer: D
NEW QUESTION 5
A company recently added a DR site and is redesigning the network. Users at the DR site are having issues browsing websites. INSTRUCTIONS
Click on each firewall to do the following:  Deny cleartext web traffic.
Deny cleartext web traffic. Ensure secure management protocols are used.
Ensure secure management protocols are used.  Resolve issues at the DR site.
Resolve issues at the DR site.
The ruleset order cannot be modified due to outside constraints.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.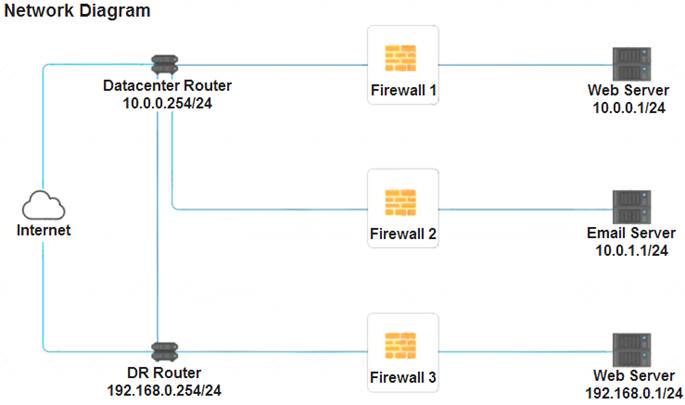
Answer: A
Explanation:
See explanation below.
Explanation
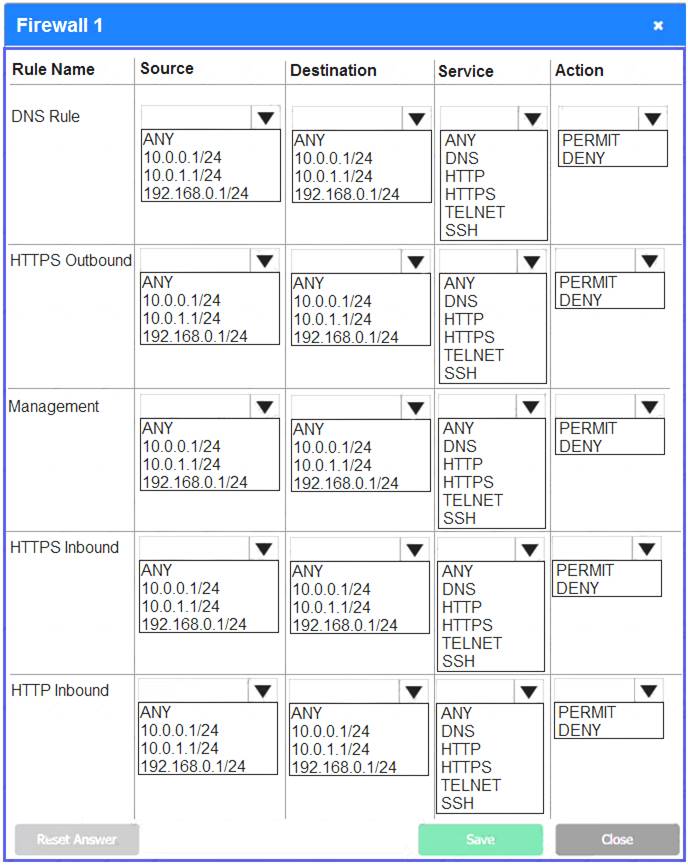
Firewall 1: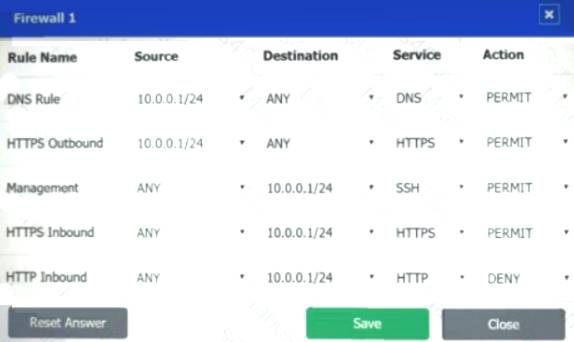
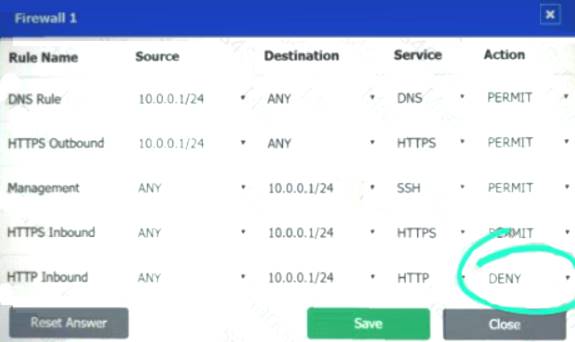
DNS Rule – ANY --> ANY --> DNS --> PERMIT
HTTPS Outbound – 10.0.0.1/24 --> ANY --> HTTPS --> PERMIT Management – ANY --> ANY --> SSH --> PERMIT
HTTPS Inbound – ANY --> ANY --> HTTPS --> PERMIT HTTP Inbound – ANY --> ANY --> HTTP --> DENY
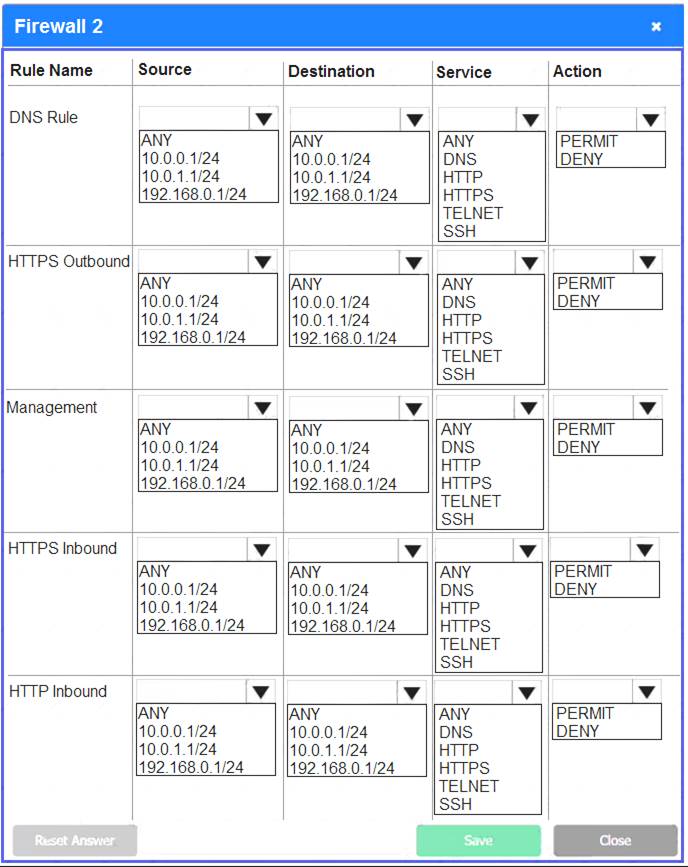
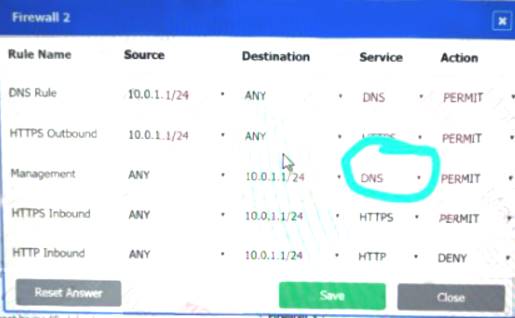
Firewall 2: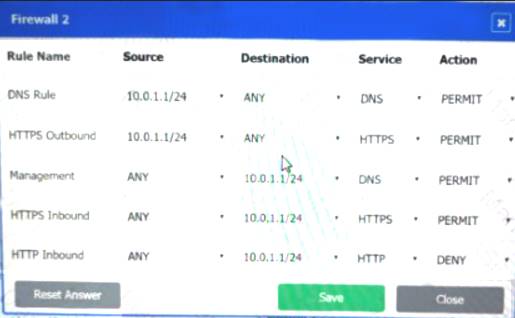
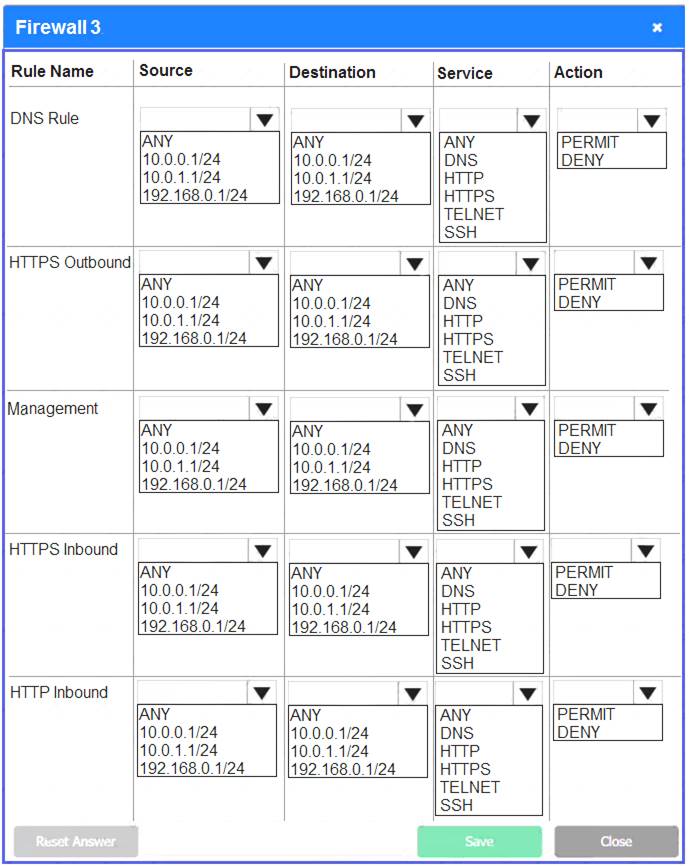
Firewall 3: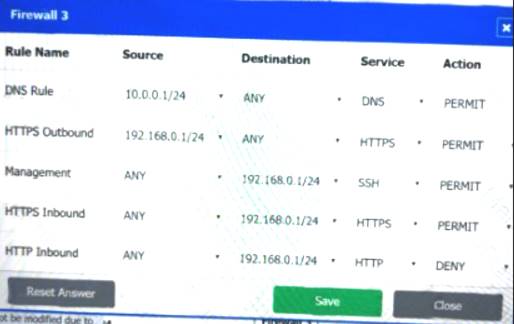
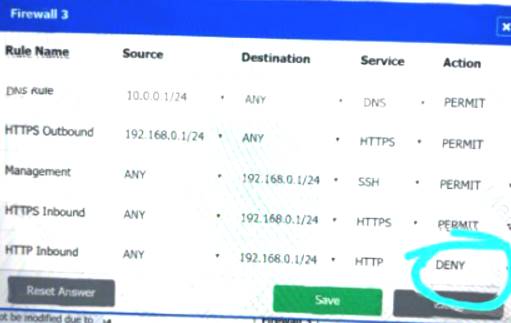
DNS Rule – ANY --> ANY --> DNS --> PERMIT
HTTPS Outbound – 192.168.0.1/24 --> ANY --> HTTPS --> PERMIT Management – ANY --> ANY --> SSH --> PERMIT
HTTPS Inbound – ANY --> ANY --> HTTPS --> PERMIT HTTP Inbound – ANY --> ANY --> HTTP --> DENY
NEW QUESTION 6
Which of the following refers to applications and systems that are used within an organization without consent or approval?
Answer: A
NEW QUESTION 7
A smart retail business has a local store and a newly established and growing online storefront. A recent storm caused a power outage to the business and the local ISP, resulting in several hours of lost sales and delayed order processing. The business owner now needs to ensure two things:
* Protection from power outages
* Always-available connectivity In case of an outage
The owner has decided to implement battery backups for the computer equipment Which of the following would BEST fulfill the owner's second need?
Answer: C
NEW QUESTION 8
A cybersecurity analyst needs to implement secure authentication to third-party websites without users’ passwords. Which of the following would be the BEST way to achieve this objective?
Answer: C
NEW QUESTION 9
A database administrator needs to ensure all passwords are stored in a secure manner, so the administrate adds randomly generated data to each password before string. Which of the following techniques BEST explains this action?
Answer: C
NEW QUESTION 10
A manufacturer creates designs for very high security products that are required to be protected and controlled by the government regulations. These designs are not accessible by corporate networks or the Internet. Which of the following is the BEST solution to protect these designs?
Answer: A
NEW QUESTION 11
A vulnerability assessment report will include the CVSS score of the discovered vulnerabilities because the score allows the organization to better.
Answer: D
NEW QUESTION 12
A Chief Information Security Officer (CISO) is concerned about the organization's ability to continue business operation in the event of a prolonged DDoS attack on its local datacenter that consumes database resources. Which of the following will the CISO MOST likely recommend to mitigate this risk?
Answer: B
NEW QUESTION 13
A cybersecurity administrator has a reduced team and needs to operate an on-premises network and security infrastructure efficiently. To help with the situation, the administrator decides to hire a service provider. Which of the following should the administrator use?
Answer: D
NEW QUESTION 14
Which of the following cloud models provides clients with servers, storage, and networks but nothing else?
Answer: C
NEW QUESTION 15
A pharmaceutical sales representative logs on to a laptop and connects to the public WiFi to check emails and update reports. Which of the following would be BEST to prevent other devices on the network from directly accessing the laptop? (Choose two.)
Answer: AB
NEW QUESTION 16
Which of the following BEST explains the reason why a server administrator would place a document named password.txt on the desktop of an administrator account on a server?
Answer: A
NEW QUESTION 17
An analyst needs to identify the applications a user was running and the files that were open before the user’s computer was shut off by holding down the power button. Which of the following would MOST likely contain that information?
Answer: C
NEW QUESTION 18
Which of the following would BEST identify and remediate a data-loss event in an enterprise using third-party, web-based services and file-sharing platforms?
Answer: D
NEW QUESTION 19
A company needs to centralize its logs to create a baseline and have visibility on its security events. Which of the following technologies will accomplish this objective?
Answer: A
NEW QUESTION 20
An organization hired a consultant to assist with an active attack, and the consultant was able to identify the compromised accounts and computers. Which of the following is the consultant MOST likely to recommend to prepare for eradication?
Answer: B
NEW QUESTION 21
In the middle of a cybersecurity, a security engineer removes the infected devices from the network and lock down all compromised accounts. In which of the following incident response phases is the security engineer currently operating?
Answer: E
NEW QUESTION 22
Which of the following is the purpose of a risk register?
Answer: C
NEW QUESTION 23
A security analyst needs to make a recommendation for restricting access to certain segments of the network using only data-link layer security. Which of the following controls will the analyst MOST likely recommend?
Answer: A
NEW QUESTION 24
......
P.S. Allfreedumps.com now are offering 100% pass ensure SY0-601 dumps! All SY0-601 exam questions have been updated with correct answers: https://www.allfreedumps.com/SY0-601-dumps.html (218 New Questions)