
we provide Top Quality CompTIA SY0-601 actual test which are the best for clearing SY0-601 test, and to get certified by CompTIA CompTIA Security+ Exam. The SY0-601 Questions & Answers covers all the knowledge points of the real SY0-601 exam. Crack your CompTIA SY0-601 Exam with latest dumps, guaranteed!
Also have SY0-601 free dumps questions for you:
NEW QUESTION 1
An organization has a growing workforce that is mostly driven by additions to the sales department. Each newly hired salesperson relies on a mobile device to conduct business. The Chief Information Officer (CIO) is wondering it the organization may need to scale down just as quickly as it scaled up. The ClO is also concerned about the organization's security and customer privacy. Which of the following would be BEST to address the ClO’s concerns?
Answer: C
NEW QUESTION 2
A company recently set up an e-commerce portal to sell its product online. The company wants to start accepting credit cards for payment, which requires compliance with a security standard. Which of the following standards must the company comply with before accepting credit cards on its e-commerce platform?
Answer: A
NEW QUESTION 3
A security analyst sees the following log output while reviewing web logs:
Which of the following mitigation strategies would be BEST to prevent this attack from being successful?
Answer: B
NEW QUESTION 4
A security analyst needs to complete an assessment. The analyst is logged into a server and must use native tools to map services running on it to the server's listening ports. Which of the following tools can BEST accomplish this talk?
Answer: B
NEW QUESTION 5
A critical file server is being upgraded and the systems administrator must determine which RAID level the new server will need to achieve parity and handle two simultaneous disk failures. Which of the following RAID levels meets this requirements?
Answer: C
NEW QUESTION 6
A user is concerned that a web application will not be able to handle unexpected or random input without crashing. Which of the following BEST describes the type of testing the user should perform?
Answer: D
NEW QUESTION 7
A user recently attended an exposition and received some digital promotional materials The user later noticed blue boxes popping up and disappearing on the computer, and reported receiving several spam emails, which the user did not open Which of the following is MOST likely the cause of the reported issue?
Answer: D
NEW QUESTION 8
A workwide manufacturing company has been experiencing email account compromised. In one incident, a user logged in from the corporate office in France, but then seconds later, the same user account attempted a login from Brazil. Which of the following account policies would BEST prevent this type of attack?
Answer: D
NEW QUESTION 9
A security administrator suspects there may be unnecessary services running on a server. Which of the following tools will the administrator MOST likely use to confirm the suspicions?
Answer: A
NEW QUESTION 10
A company is adopting a BYOD policy and is looking for a comprehensive solution to protect company information on user devices. Which of the following solutions would BEST support the policy?
Answer: A
NEW QUESTION 11
A security administrator checks the table of a network switch, which shows the following output: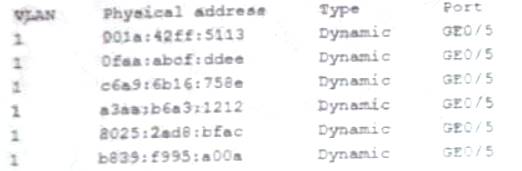
Which of the following is happening to this switch?
Answer: A
NEW QUESTION 12
A startup company is using multiple SaaS and IaaS platforms to stand up a corporate infrastructure and build out a customer-facing web application. Which of the following solutions would be BEST to provide security, manageability, and visibility into the platforms?
Answer: C
NEW QUESTION 13
The SOC is reviewing process and procedures after a recent incident. The review indicates it took more than 30 minutes to determine that quarantining an infected host was the best course of action. The allowed the malware to spread to additional hosts before it was contained. Which of the following would be BEST to improve the incident response process?
Answer: A
NEW QUESTION 14
A security analyst needs to implement an MDM solution for BYOD users that will allow the company to retain control over company emails residing on the devices and limit data exfiltration that might occur if the devices are lost or stolen. Which of the following would BEST meet these requirements? (Select TWO).
Answer: AB
NEW QUESTION 15
Which of the following is MOST likely to outline the roles and responsibilities of data controllers and data processors?
Answer: C
NEW QUESTION 16
Which of the following describes the BEST approach for deploying application patches?
Answer: A
NEW QUESTION 17
A technician needs to prevent data loss in a laboratory. The laboratory is not connected to any external networks. Which of the following methods would BEST prevent the exfiltration of data? (Select TWO).
Answer: BE
NEW QUESTION 18
A consultant is configuring a vulnerability scanner for a large, global organization in multiple countries. The consultant will be using a service account to scan systems with administrative privileges on a weekly basis, but there is a concern that hackers could gain access to account to the account and pivot through the global network. Which of the following would be BEST to help mitigate this concern?
Answer: C
NEW QUESTION 19
Which of the following job roles would sponsor data quality and data entry initiatives that ensure business and regulatory requirements are met?
Answer: C
NEW QUESTION 20
An analyst visits an internet forum looking for information about a tool. The analyst finds a threat that appears to contain relevant information. One of the posts says the following:
Which of the following BEST describes the attack that was attempted against the forum readers?
Answer: C
NEW QUESTION 21
A security engineer needs to enhance MFA access to sensitive areas in a building. A key card and fingerprint scan are already in use. Which of the following would add another factor of authentication?
Answer: B
NEW QUESTION 22
A network technician is installing a guest wireless network at a coffee shop. When a customer purchases an Item, the password for the wireless network is printed on the recent so the customer can log in. Which of the following will the technician MOST likely configure to provide the highest level of security with the least amount of overhead?
Answer: A
NEW QUESTION 23
A security analyst discovers several .jpg photos from a cellular phone during a forensics investigation involving a compromised system. The analyst runs a forensics tool to gather file metadata. Which of the following would be part of the images if all the metadata is still intact?
Answer: A
NEW QUESTION 24
......
Thanks for reading the newest SY0-601 exam dumps! We recommend you to try the PREMIUM 2passeasy SY0-601 dumps in VCE and PDF here: https://www.2passeasy.com/dumps/SY0-601/ (218 Q&As Dumps)