
Your success in CompTIA SY0-601 is our sole target and we develop all our SY0-601 braindumps in a way that facilitates the attainment of this target. Not only is our SY0-601 study material the best you can find, it is also the most detailed and the most updated. SY0-601 Practice Exams for CompTIA SY0-601 are written to the highest standards of technical accuracy.
Check SY0-601 free dumps before getting the full version:
NEW QUESTION 1
An organization just experienced a major cyberattack modem. The attack was well coordinated sophisticated and highly skilled. Which of the following targeted the organization?
Answer: D
NEW QUESTION 2
A security engineer is reviewing log files after a third discovered usernames and passwords for the organization’s accounts. The engineer sees there was a change in the IP address for a vendor website one earlier. This change lasted eight hours. Which of the following attacks was MOST likely used?
Answer: D
NEW QUESTION 3
Accompany deployed a WiFi access point in a public area and wants to harden the configuration to make it more secure. After performing an assessment, an analyst identifies that the access point is
configured to use WPA3, AES, WPS, and RADIUS. Which of the following should the analyst disable to enhance the access point security?
Answer: D
NEW QUESTION 4
An analyst visits an internet forum looking for information about a tool. The analyst finds a threat that appears to contain relevant information. One of the posts says the following:
Which of the following BEST describes the attack that was attempted against the forum readers?
Answer: C
NEW QUESTION 5
A public relations team will be taking a group of guest on a tour through the facility of a large e-commerce company. The day before the tour, the company sends out an email to employees to ensure all whiteboars are cleaned and all desks are cleared. The company is MOST likely trying to protect against.
Answer: C
NEW QUESTION 6
Which of the following is MOST likely to outline the roles and responsibilities of data controllers and data processors?
Answer: C
NEW QUESTION 7
A university with remote campuses, which all use different service providers, loses Internet connectivity across all locations. After a few minutes, Internet and VoIP services are restored, only to go offline again at random intervals, typically within four minutes of services being restored. Outages continue throughout the day, impacting all inbound and outbound connections and services. Services that are limited to the local LAN or WiFi network are not impacted, but all WAN and VoIP services are affected.
Later that day, the edge-router manufacturer releases a CVE outlining the ability of an attacker to exploit the SIP protocol handling on devices, leading to resource exhaustion and system reloads. Which of the following BEST describe this type of attack? (Choose two.)
Answer: AD
NEW QUESTION 8
A company has drafted an insider-threat policy that prohibits the use of external storage devices. Which of the following would BEST protect the company from data exfiltration via removable media?
Answer: D
NEW QUESTION 9
A company is upgrading its wireless infrastructure to WPA2-Enterprise using EAP-TLS. Which of the following must be part of the security architecture to achieve AAA? (Select TWO)
Answer: EF
NEW QUESTION 10
Joe, a user at a company, clicked an email link led to a website that infected his workstation. Joe, was connected to the network, and the virus spread to the network shares. The protective measures failed to stop this virus, and It has continues to evade detection. Which of the following should administrator implement to protect the environment from this malware?
Answer: C
NEW QUESTION 11
When selecting a technical solution for identity management, an architect chooses to go from an in-house to a third-party SaaS provider. Which of the following risk management strategies is this an example of?
Answer: D
NEW QUESTION 12
Phishing and spear-phishing attacks have been occurring more frequently against a company’s staff. Which of the following would MOST likely help mitigate this issue?
Answer: C
NEW QUESTION 13
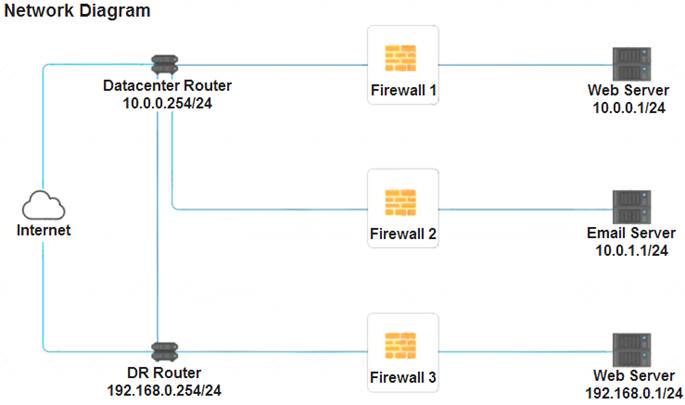
A company recently added a DR site and is redesigning the network. Users at the DR site are having issues browsing websites.
INSTRUCTIONS
Click on each firewall to do the following:
Deny cleartext web traffic.
Ensure secure management protocols are used.
Resolve issues at the DR site.
The ruleset order cannot be modified due to outside constraints.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.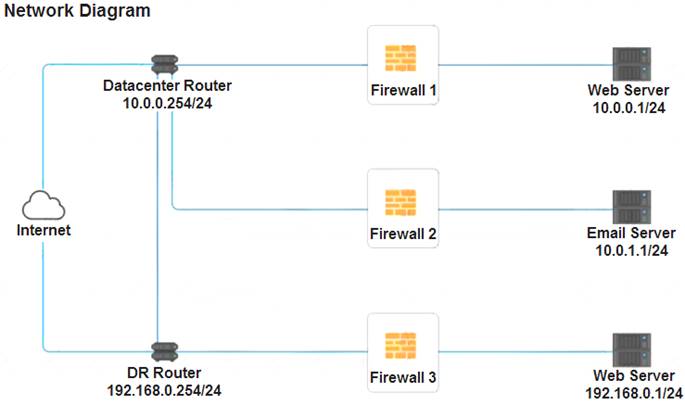
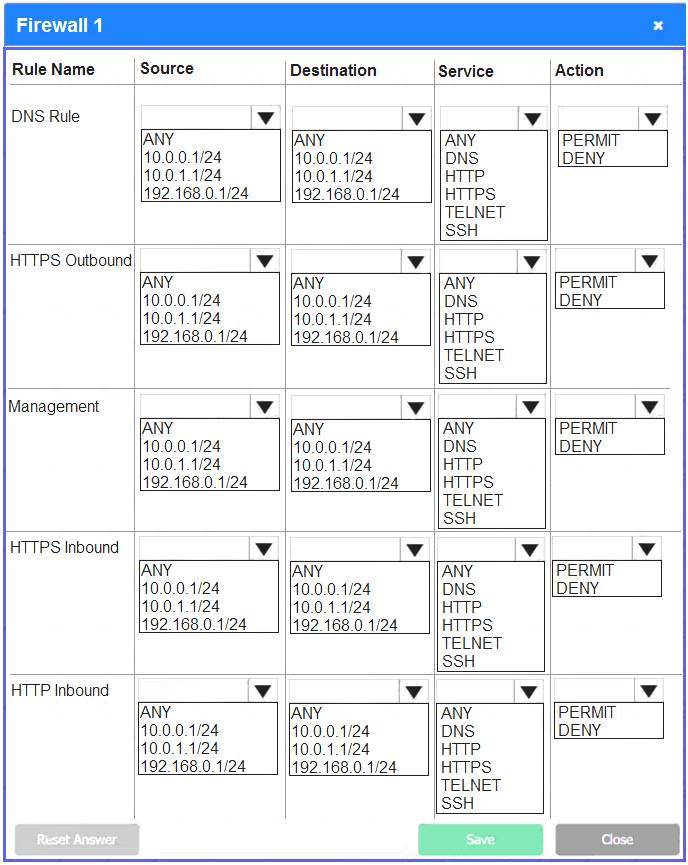
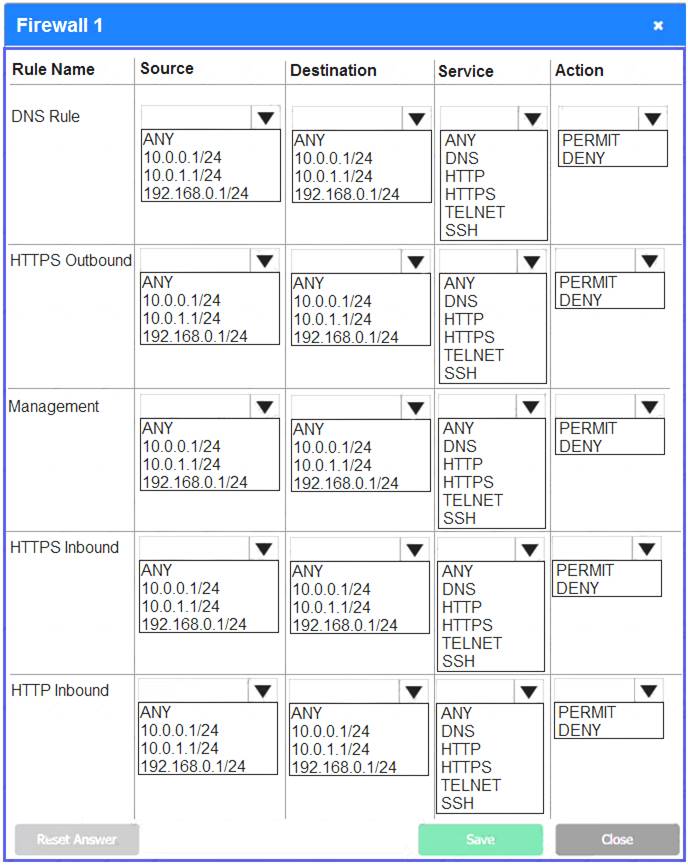
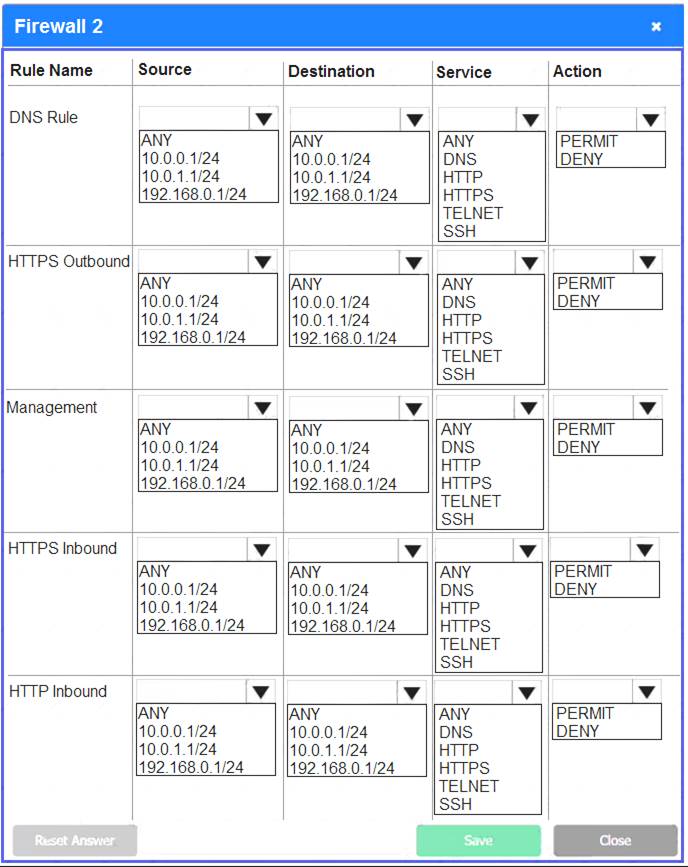
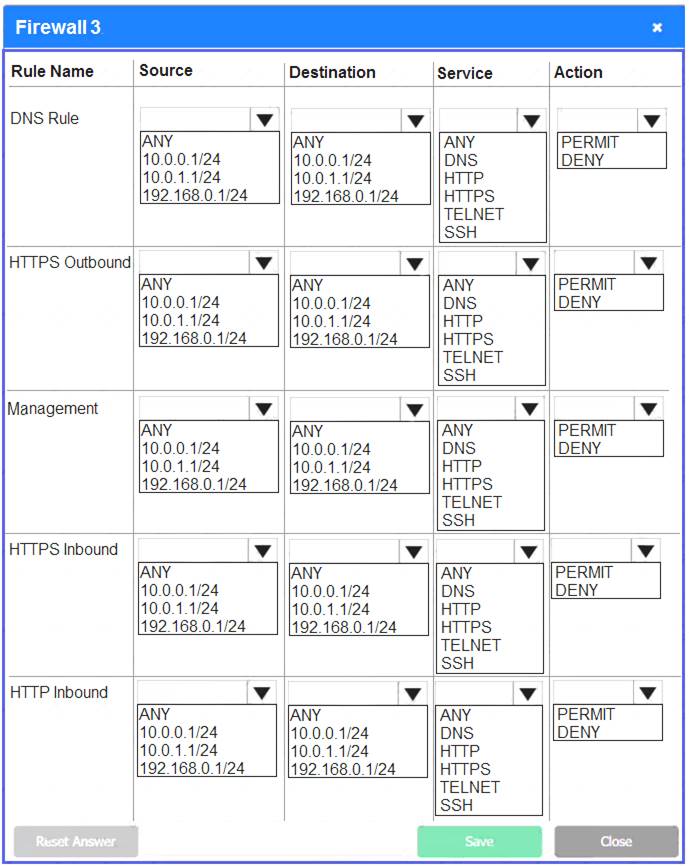
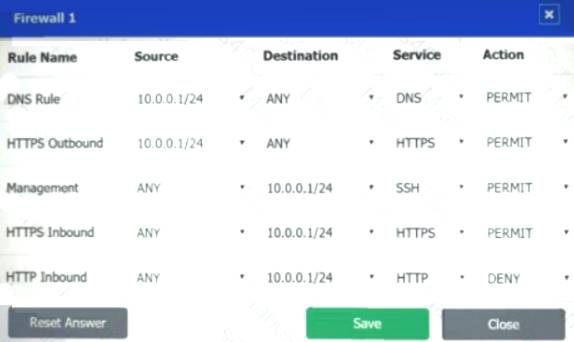
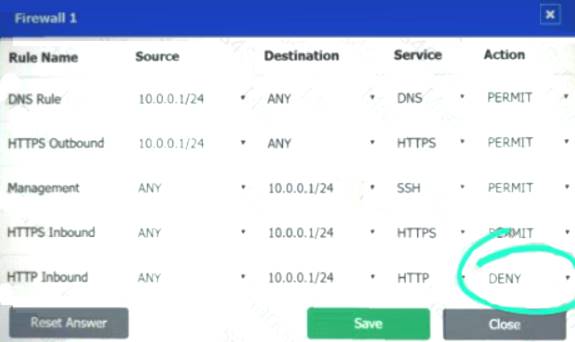
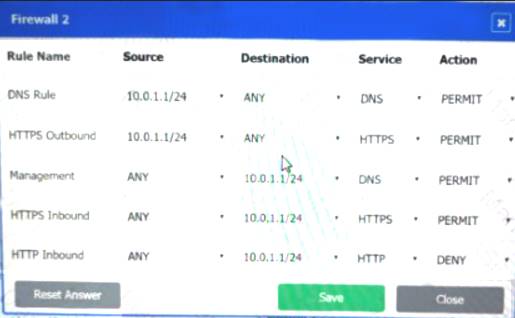
Answer: A
NEW QUESTION 14
A global company is experiencing unauthorized logging due to credential theft and account lockouts caused by brute-force attacks. The company is considering implementing a third-party identity provider to help mitigate these attacks. Which of the following would be the BEST control for the company to require from prospective vendors’?
Answer: B
NEW QUESTION 15
The SOC is reviewing process and procedures after a recent incident. The review indicates it took more than 30 minutes to determine that quarantining an infected host was the best course of action. The allowed the malware to spread to additional hosts before it was contained. Which of the following would be BEST to improve the incident response process?
Answer: A
NEW QUESTION 16
An organization with a low tolerance for user inconvenience wants to protect laptop hard drives against loss or data theft. Which of the following would be the MOST acceptable?
Answer: A
NEW QUESTION 17
An organization relies on third-party video conferencing to conduct daily business. Recent security changes now require all remote workers to utilize a VPN to corporate resources. Which of the following would BEST maintain high-quality video conferencing while minimizing latency when connected to the VPN?
Answer: D
NEW QUESTION 18
......
Thanks for reading the newest SY0-601 exam dumps! We recommend you to try the PREMIUM Certshared SY0-601 dumps in VCE and PDF here: https://www.certshared.com/exam/SY0-601/ (402 Q&As Dumps)